3.1 KiB
Difficulty
Easy
Category
Stegenography
How To Solve
When trying to unzip hahah.zip, you need to enter a password. Since no other files are provided, you will need to brute-force the password. You may have noticed the hint in the challenge description, saying that John is often called 'John The Zipper'. This refers to the open source password cracking tool 'John The Ripper'. Using the zip2john command, you can obtain the password hash. If you then use john with that hash, it will crack the password.
> zip2john hahah.zip > hash.txt
ver 2.0 efh 5455 efh 7875 hahah.zip/hahah.johnmeme PKZIP Encr: TS_chk, cmplen=1157853, decmplen=1158716, crc=AA183960 ts=53A1 cs=53a1 type=8
> john hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 8 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
Proceeding with incremental:ASCII
1652 (hahah.zip/hahah.johnmeme)
1g 0:00:00:00 DONE 3/3 (2023-10-31 10:33) 1.136g/s 2289Kp/s 2289Kc/s 2289KC/s rrg84..cybo07
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Use the password (1652) to unzip the file. You now have access to the contained file, called hahah.johnmeme. Since this is a somewhat weird extension, you'll have to figure out the file type.
> file hahah.johnmeme
hahah.johnmeme: PNG image data, 640 x 642, 8-bit/color RGBA, non-interlaced
If you open the file, you can see that it is indeed an image. However, the flag is still not captured. Also, it is not hidden in this image. Where else can it be?
To continue, you have to find out that the hahah.johnmeme contains more than only an image. To uncover all embedded data types, you can use a tool called binwalk.
> binwalk hahah.johnmeme
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 640 x 642, 8-bit/color RGBA, non-interlaced
140 0x8C Zlib compressed data, best compression
436168 0x6A7C8 gzip compressed data, has original file name: "hahah.xcf", from Unix
Besides a PNG image, this file appears to also contain Zlib end gzip compressed data. You can ignore the Zlib data, since this is associated with the PNG image. However, the gzip compressed data looks interesting as the original filename was hahah.xcf. If you now use the same command, but with -e, the data will be extracted from the hahah.johnmeme file to the _hahah.johnmeme.extracted folder.
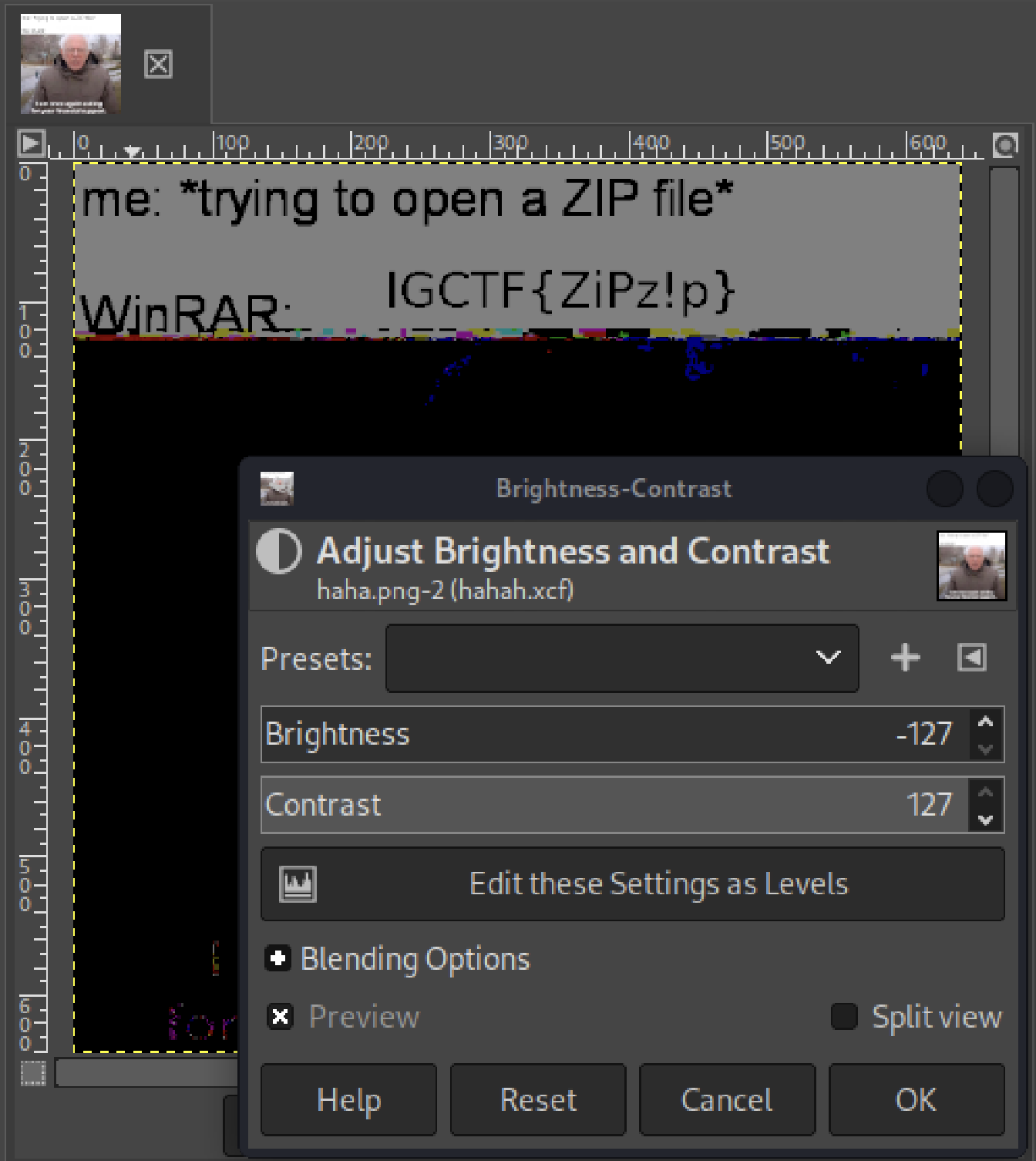
In this folder, you can see the hahah.xcf file (notice that you don't have to unzip the .gz file anymore). XCF is the native image format of GIMP. Open the file in GIMP and you will see the same meme. Go to Colors > Brightness-Contrast, decrease the Brightness all the way down, and increase the Contrast all the way up. The flag should now be visible.
Flag
IGCTF{ZiPz!p}